Icmp Flood Ip | Ping flood, also known as icmp flood, is a common denial of service (dos) attack in which an attacker takes down a victim's computer by overwhelming it with icmp echo requests, also known as pings. A ping flood involves flooding a target computer with icmp echo request packets. An internet control message protocol (icmp) flooding attack (schubaet al., 1997) comprises of a stream of icmp echo packets generated by the attackers and aimed at the victim. In this case the victim server is flooded with fabricated icmp packets from a wide range of ip addresses. The value set in the alert, activate, and maximum fields is the packets per second from one or many hosts to one or many destinations in the zone.
The threshold must be set carefully as too small a threshold may affect unintented traffic and too large a threshold may not effectively protect from an attack. Other icmp messages also include destination host unreachable, fragmentation required, congestion control, ttl exceeded, ip protocol errors, and an number of others. The network's bandwidth is quickly used up and prevents legitimate packets from getting through to their destination. In terms of the technology, the ping flood is based on the internet control message protocol (icmp). Also, what is icmp attack?
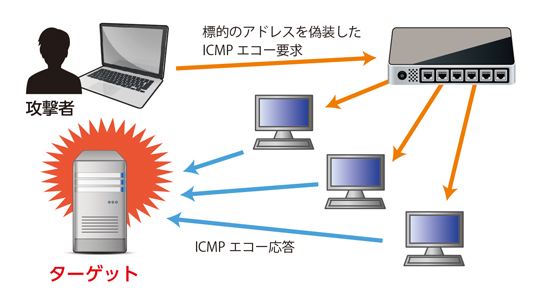
The ip of the attacker and the victim Dos icmp flood on c6300. This protocol and the associated ping command are generally used to perform network tests. Unlike in tcp, icmp packets do not require confirmation of receipt therefore detecting junk traffic in icmp. The internet control message protocol (icmp), which is utilized in a ping flood attack, is an internet layer protocol used by network devices to communicate. In terms of the technology, the ping flood is based on the internet control message protocol (icmp). Ping flood, also known as icmp flood, is a common denial of service (dos) attack in which an attacker takes down a victim's computer by overwhelming it with icmp echo requests, also known as pings. An internet control message protocol (icmp) flooding attack (schubaet al., 1997) comprises of a stream of icmp echo packets generated by the attackers and aimed at the victim. You should examine your router's log file to determine if this is the case. In this method, the perpetrators send large numbers of ip packets with the source addresses appearing as the address of the victim. Also, what is icmp attack? Flood using syn packets against port 80: In this case the victim server is flooded with fabricated icmp packets from a wide range of ip addresses.
A good example of this is a worm attack, such as an attack by the sql slammer worm. Ping flood, also known as icmp flood, is a common denial of service (dos) attack in which an attacker takes down a victim's computer by overwhelming it with icmp echo requests, also known as pings. In this method, the perpetrators send large numbers of ip packets with the source addresses appearing as the address of the victim. The internet control message protocol (icmp) utilized during a ping flood attack, is an internet layer protocol used by network devices to communicate with each other. Other icmp messages also include destination host unreachable, fragmentation required, congestion control, ttl exceeded, ip protocol errors, and an number of others.
![] ЯЊ~Ҳ™ : Ataques DoS, Syn, ICMP, UDP Flood](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgx7ddC9d5ZtilFjRgaumdunRm0fsDiVnUvL9RI74JQ9-Ba8lQKunYKxsA-A7nfKElHYWfxWFs241q3lghemlxiCDUVoBjBfTbHIOhwx4gvMVMHsDD9TsVzPQY-jMAgi4hU5aRgLptuSVyT/s1600/smurf-attack.jpg)
As seen in the image 1 an icmp flood of type 8 consists of a high volume of icmp echo packets. These packets have a source ip (which is normally spoofed to reduce the effect of ip reputation mechanisms) and the destination ip of the victim. In this method, the perpetrators send large numbers of ip packets with the source addresses appearing as the address of the victim. Choosable dns/ip, port, page, server timeout, threads, time between headers. The threshold must be set carefully as too small a threshold may affect unintented traffic and too large a threshold may not effectively protect from an attack. You should receive the same number of icmp echo responses. The malefactor aims to fill the channel and overload the victim server with fake requests. A good example of this is a worm attack, such as an attack by the sql slammer worm. An internet control message protocol (icmp) flooding attack (schubaet al., 1997) comprises of a stream of icmp echo packets generated by the attackers and aimed at the victim. The internet control message protocol (icmp) utilized during a ping flood attack, is an internet layer protocol used by network devices to communicate with each other. You should examine your router's log file to determine if this is the case. Icmp rate limiting many attacks create a dos attack by sending a flood of traffic to a device or devices that do not exist, causing an intervening router to reply back with an icmp unreachable message for each unknown destination. Other icmp messages also include destination host unreachable, fragmentation required, congestion control, ttl exceeded, ip protocol errors, and an number of others.
The network's bandwidth is quickly used up and prevents legitimate packets from getting through to their destination. A zone protection profile with flood protection configured defends an entire ingress zone against syn, icmp, icmpv6, udp, and other ip flood attacks. Packet flood generator as the name stands is a projet to produce a threaded traffic generator program, it has support for generating ip, tcp , udp, icmp and igmp packets, also has as feature to keep the connection up. Dos icmp flood on c6300. The malefactor aims to fill the channel and overload the victim server with fake requests.

Port 80, you can replace this number for the service you want to attack. Failure to receive as many packets as were sent or a round trip time that is too high can indicate problems on the network. If an external ddos icmp flood attack is occurring, you need to create a router firewall rule, assuming your router has a configurable firewall, to block all inbound traffic for the ip addresses that are the source of the ddos attack. Under flood protection, you can configure your device for protection from syn floods, udp floods, icmp floods and other ip floods. Comcast has suggested that to fix the problem i would need to replace the modem. You should receive the same number of icmp echo responses. An icmp flood ddos attack requires that the attacker knows the ip address of the target. A ping flood attack sends icmp echo request packets as fast as possible without waiting for a reply in an attempt to overload the server. These packets have a source ip (which is normally spoofed to reduce the effect of ip reputation mechanisms) and the destination ip of the victim. Icmp rate limiting many attacks create a dos attack by sending a flood of traffic to a device or devices that do not exist, causing an intervening router to reply back with an icmp unreachable message for each unknown destination. The malefactor aims to fill the channel and overload the victim server with fake requests. An internet control message protocol (icmp) flooding attack (schubaet al., 1997) comprises of a stream of icmp echo packets generated by the attackers and aimed at the victim. To avoid this kind of situation, network administrators usually block icmp on their network.
Icmp Flood Ip: In this case the victim server is flooded with fabricated icmp packets from a wide range of ip addresses.